Simple Usage Tools Cobalt Strike Horse
tags: cobalt strike Red Team
For HW, a lot of red team developers are simply processed down the CS horses, set the layer housing, and extract CS for the analysis of this sample, you can use tools to quickly analyze the cs's Beacon, do n'thing too much.
First get the sample, first extract the malicious PE file. Use the PE-SIEVE tool.
https://github.com/hasherezade/pe-sieve
For example, this unnamed is the horse.
If you have a few layers, you can go down to the key API, manual DUMP out of memory, but most of the samples in China are simple construction.
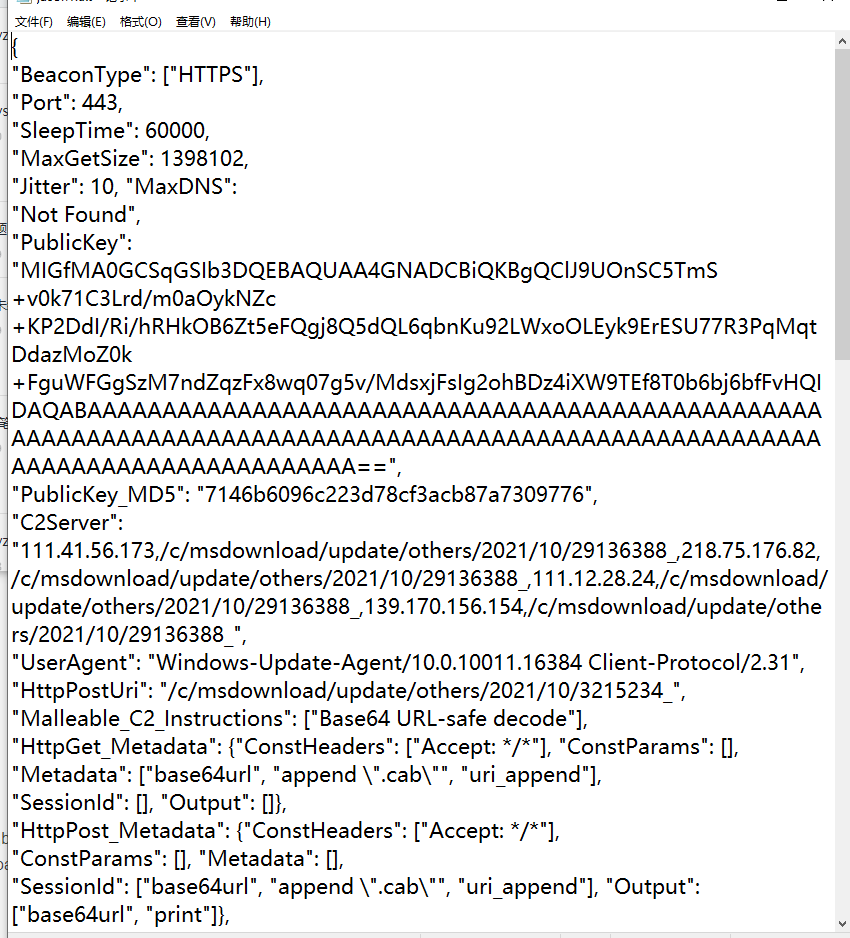
Rethink if the malicious code is Cobaltstrike, such as an example here, IDA sees a different or operation.
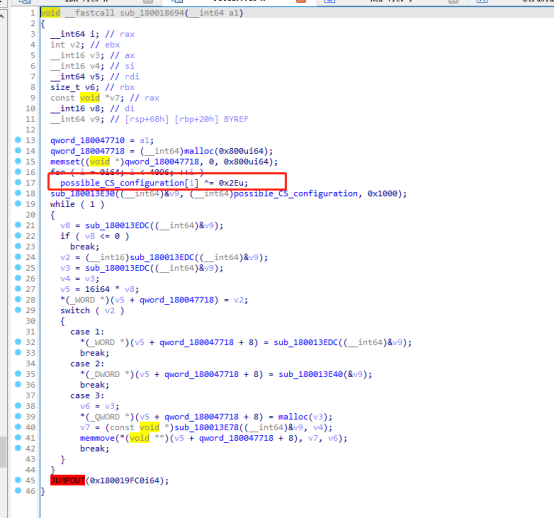
Extract data
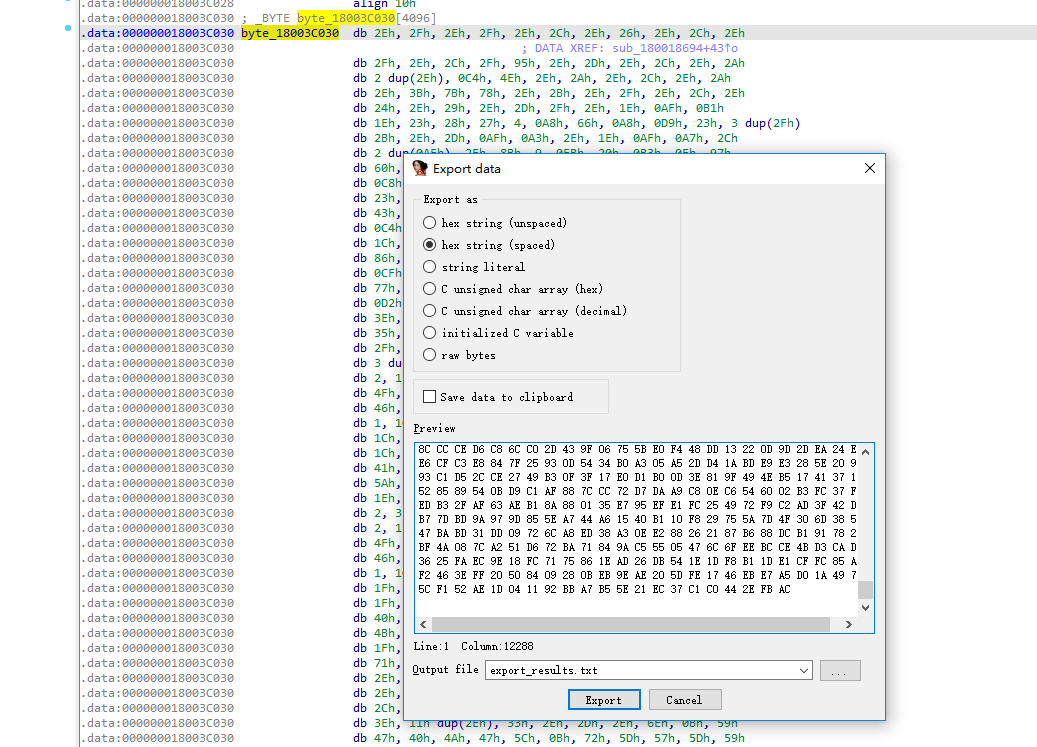
decoding
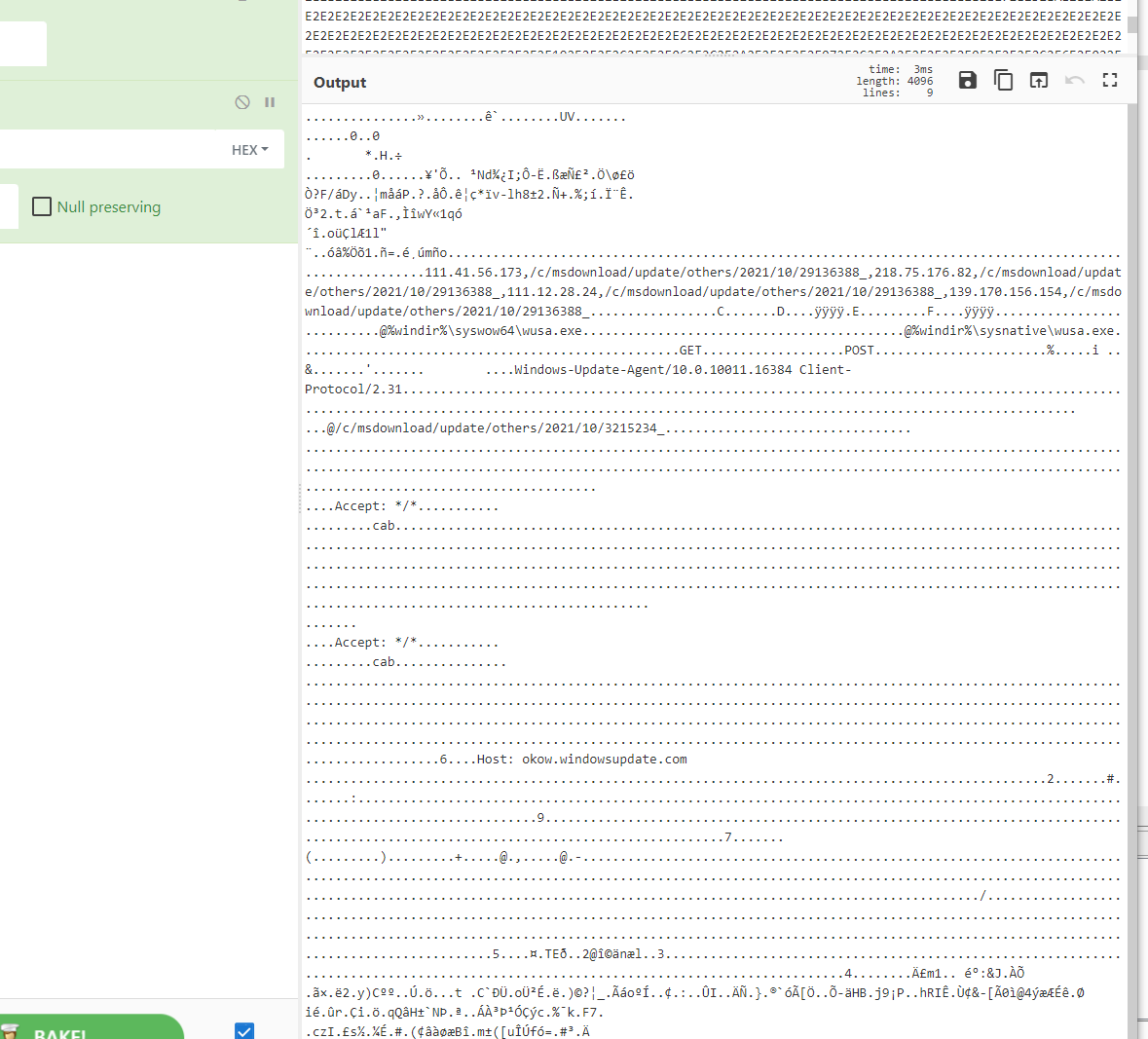
It was found that it is a CS configuration, and then use COBALTSTRIKEPARSER to resolve Beacon, it can also be used without brain. If you report an error, change other ideas, but HW samples are mostly in the CS horse.
The tool link is as follows:
https://github.com/Sentinel-One/CobaltStrikeParser
Intelligent Recommendation
How to use Cobalt Strike
Cobalt Strike is a GUI framework penetration testing tool based on Metasploit, which integrates port forwarding, service scanning, automatic overflow, multi-mode port monitoring, exe, powershell Tro...
Cobalt Strike installation
1. Supported platforms Because the cobalt strike is based on java, it can run on windows, linux, macos and other systems. Here I choose to install on linux, put the compressed package in linux an...
Cobalt Strike environment construction
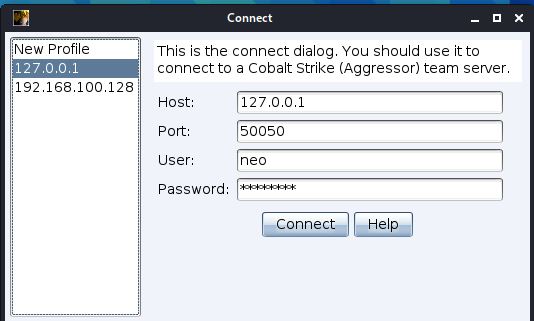
Environment setup Set up a team server to connect with the client. Service-Terminal Here, the kali virtual machine is used as the server address. First you need to know the IP address of the serverifc...
cobalt strike use (1)
background I installed the cs two days ago. Today, I took advantage of the weekend to try how to use it, but after a long time I did not successfully launch the target drone. Change the method and the...
Cobalt strike plugin development
Pay attention to the safety and share the latest network security knowledge. 0x01 AGScript Introduction agscriptforAggressor ScriptShorthand. agscriptYesCobaltStrike 3.0Script lan...
More Recommendation
Cobalt strike target
Environmental construction Server side: Kali Client: Win10 Target machine: Win7 Note: CS is based on the Java environment, first install Java, JDK1.8 CS installation After installation Give TeamServer...
Cobalt Strike Environment
Cobalt Strike Environment 0x01 Cobalt Strike Introduction Cobalt Strike is a permeate test artifact developed by US Red Team, called CS by people in the circle. CS is divided into server and client, f...
NO4.COBALT STRIKE (on)
🥝cobalt strike is a permeate test artifact developed by US Red Team, often known as CS. Recently, this tool fire has become an indispensable tool in penetration test. It has a variety of protocol hos...
About Cobalt Strike
About Cobalt Strike CobaltStrike About Cobalt Strike Cobalt Strike APT attack Give Team Server and Cobalt Strike to give execution permissions About Cobaltstrike folder Start Team Server and client Co...
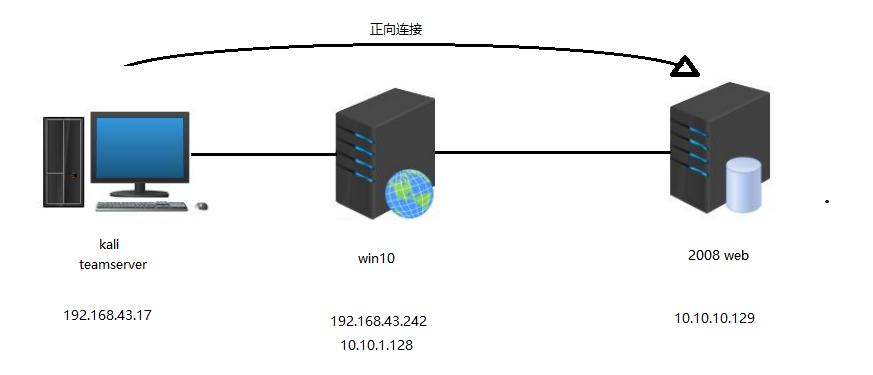
Cobalt strike is in reverse connection
Use the Cobalt strike to connect multiple layers Use the Cobalt strike to connect multiple layers Win10 server is online to CS, using Win10 as a stripper forward connection 2008WEB server Generate lis...